Sometimes it seems like this blog is all PKI, all the time. It’s really not, although I’ll have to admit a bit of an obsession recently with making sure all of my certificates were in order. I’ve taken care of Kibana, my EdgeOS router, and my TPLink switch, but there was one tool I used that was throwing errors and it was annoying me: the Unifi Network web app. So I decided that I had to fix it, and it wasn’t much trouble at all.
About Unifi Web
I have the Unifi web app running on one of my Linux boxes. It’s a Java app, which means that unlike the other certificates I’ve been dealing with, which have been in PEM format, this is a Java keystore. Fortunately, I’ve some experience with Java keystores from my day job, where some of our app runs on Java. The main tool for interfacing with keystores is keytool, which allows you to create and modify keystores.
Updating the Certificate
To start, I generated a private key, then a CSR similar to what I’ve done before. The next step was to grab the keystore used by Unifi, which is at /var/lib/unifi/keystore. I made a copy of it just in case, then the fun began.
My next step was to import the trusted root and intermediate certs that make up the chain. To do so, I grabbed the root and intermediate certs (NOT the private keys of course), and ran the following:
keytool -import -trustcacerts -alias root -file ./root.crt -keystore ./keystore
keytool -import -trustcacerts -alias intermediate -file ./ia.crt -keystore ./keystoreKeystores have a password, and the default password for Unifi is aircontrolenterprise.
Although importing trusted CA certs from CRT files is easy using keytool, importing a cert/private key pair is oddly not. So the next step was to convert the cert and key into a PKCS12-formatted file using openssl:
openssl pkcs12 -export -in server.crt -inkey server.key -out server.p12 -name serverThat prompts for a password; remember it for the next command. We can now convert that PKCS12-formatted file to a Java keystore file:
keytool -importkeystore -deststorepass changeme -destkeypass changeme -destkeystore server.keystore -
srckeystore server.p12 -srcstoretype PKCS12 -srcstorepass changeme -alias serverPutting It Together
Almost there! Another word about Java keystore files: each object has an alias, as you may have noticed in the commands above. The alias for the cert/key pair used by the Unifi Network app is unifi. However, since you can’t import a new pair using that alias as it is already in use, we’ll import the server object we just created, delete the existing unifi object, then rename the new one:
keytool -importkeystore -srckeystore ./server.keystore -destkeystore keystore
keytool -delete -alias unifi -keystore ./keystore
keytool -changealias -alias server -destalias unifi -keystore ./keystoreI restarted the Unifi service, et voilà!
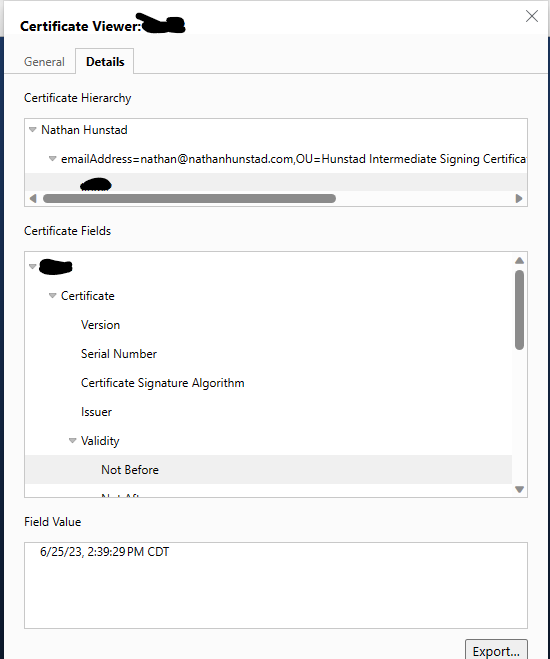
A valid cert using my own internal PKI. No more nasty browser warnings for me.
